When it comes to the safety of your data and technology systems, it’s vital that your organization recognizes the reality of the “information security lifecycle.” By its very name, the info security lifecycle indicates that true information security is a process, not a “one and done” solitary project. Information security has no end-point, and your operational framework should always strive to acknowledge that fact.
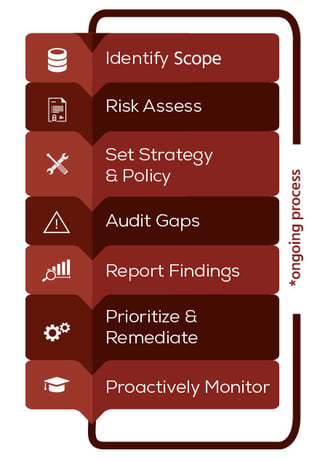
At Garland Heart, we use a lifecycle model that serves as a useful baseline to help build a solid foundation for any security program across any type of organization and industry focus. Using the lifecycle model can provide you with a road map to ensure that your information security is continually being improved. As with any other aspect of your security program, implementing the security lifecycle requires certain policies and standards. The Garland Heart lifecycle model differs depending on the type of process framework that your organization uses, but, in general, it adheres to the COBIT model (Control Objectives for Information and Related Technology) created by the Information Systems Audit and Control Association (ISACA).
As with any other aspect of your security program, implementing the security lifecycle requires certain policies and standards. The Garland Heart lifecycle model differs depending on the type of process framework that your organization uses, but, in general, it adheres to the COBIT model (Control Objectives for Information and Related Technology) created by the Information Systems Audit and Control Association (ISACA).
The information security lifecycle is broken down into four key phases:
Planning and Organization
You can start by thoroughly mapping out your network. Identify all of its key components, including individual servers, the networking infrastructure that connects those servers and the software running on them.
To get the most out of your mapping efforts, start at the highest level and drill down. Begin by identifying the basic function of the various sectors in your network, such as areas related primarily to software development, or areas dedicated to e-commerce support. Don’t forget purely internally focused systems, like those used by your human resources or accounting departments.
Next, start drilling down into each node of your network. Gather information related to the operating systems being run by each individual computer, then the applications and other software run on those computers. You should even go down deep enough to identify and list what software versions are being run on individual systems, and what specific patches and software hotfixes have been applied on each PC.
Don’t forget to include mobile technology in your efforts. Each smartphone, pad or other device that interacts with your systems should be recorded and categorized just like your desktops and standalone boxes.
Acquire and Implement
The first step is to perform a thorough vulnerability assessment that covers the entirety of your systems, from the highest level to the lowest. You should focus especially on any areas that your previous mapping efforts identified as having risk-factors, such as very outdated software versions or obsolete hardware technology.
Next, begin acquiring all of the tools that will be necessary to implement your security measures. Those tools may be security programs like firewalls, new network hardware or software that will be used to monitor and maintain your security routines once they’re in place.
This is also the time to examine how your servers are configured. Ensure their configurations match with your new policies, and especially that they are compliant with all regulatory and legal requirements.
Deliver and Support
Configure and update every system, hardware and network component, providing technical support when and where it’s necessary. You should also make sure that your security is strengthened in every aspect to comply with corporate policy, especially when it comes to password security. This is especially true when it comes to personnel, who will need to be educated about the new policies and how they will be expected to support and maintain the new security regime.
Monitor and Evaluate
In this phase, you should deploy your monitoring routines, which typically involve automated systems calibrated to detect problems, along with hands-on oversight from network administrators.
In the early phases of monitoring, your goal is to evaluate how effective all of your information security systems are by examining them according to your new procedures. Always strive to work with the “most to least” rubric discussed above, where the most critical and/or vulnerable systems receive the highest degree of scrutiny. Also, don't forget to have a qualified firm test and/or audit your environment to ensure that controls and processes are working as expected.
Once you’ve implemented the information security lifecycle, your organization will find itself even better prepared for future concerns, and will be able to adapt to changes in the security landscape much more effectively.
To find out how the information security lifecycle can keep your organization safe, contact Garland Heart for a consultation today.



